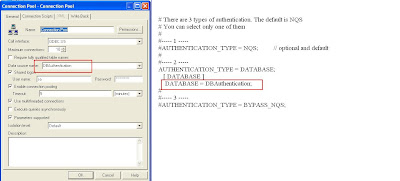
We can restrict any user from accessing the Connection Pool using the Permission option in Connection Pool.
Just click on the Permission button, then you will get "Permission - Connection Pool " window. By default, this window will show only user Groups. To see users also, check the Show all users/groups option.
For each user and group, you can allow or disallow access privileges for an object by clicking in the check box to toggle among the following options:
In the above picture, we can find one user group (Test) and two users (U1,U2). Now, let us deny access to the Group called Test.To deny access, just make the check box cross (X), as shown below.
All the users of that group cant access the connection pool. That is when the user runs a report, then he will get an error like : [nQSError: 19007] The user does not have sufficient privilege to access the database
Note : Assume that,
you have created two connection pools(eg. CP1 and CP2) for a Data source in the physical layer,
and you have a user called U1 and you have denied access to the connection Pool C1.
When a user U1 requests connection, as the user don not have permission to Connection pool C1,
OBI Server will route the request to the second Connection Pool C2. So, If you want any user to be denied to access the underlying data source, remove access to all connection poll, not any single connection pool.
Just click on the Permission button, then you will get "Permission - Connection Pool " window. By default, this window will show only user Groups. To see users also, check the Show all users/groups option.
For each user and group, you can allow or disallow access privileges for an object by clicking in the check box to toggle among the following options:
- A check mark indicates that a permission is granted.
- An X indicates that a permission is denied.
- An empty check box indicates that a permission has not been modified.
In the above picture, we can find one user group (Test) and two users (U1,U2). Now, let us deny access to the Group called Test.To deny access, just make the check box cross (X), as shown below.
All the users of that group cant access the connection pool. That is when the user runs a report, then he will get an error like : [nQSError: 19007] The user does not have sufficient privilege to access the database
Note : Assume that,
you have created two connection pools(eg. CP1 and CP2) for a Data source in the physical layer,
and you have a user called U1 and you have denied access to the connection Pool C1.
When a user U1 requests connection, as the user don not have permission to Connection pool C1,
OBI Server will route the request to the second Connection Pool C2. So, If you want any user to be denied to access the underlying data source, remove access to all connection poll, not any single connection pool.